Operating System Structure
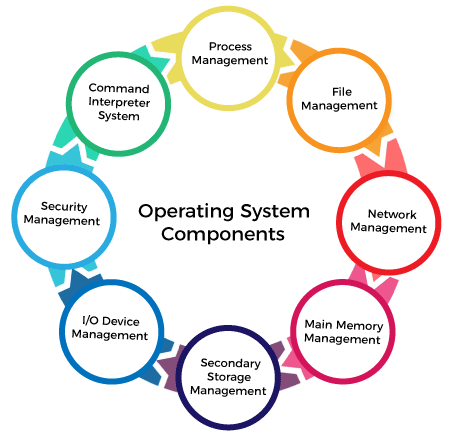
Key Components
-
Process Management
- Create/Delete Processes
- Suspend/Resume Processes
- Process Synchronization
- Process Communication
- Deadlock Handling
-
Memory Management
- Track Memory
- Allocate/Deallocate Memory
- Memory Allocation
-
Secondary Storage Management
- Disk Management
- Manage Free Space
- Storage Allocation
- Disk Scheduling
-
I/O System Management
- Buffering
- Device-Driver Interface
- Proprietary Drivers
-
File Management
- File/Directory Management
- Basic File Operations
- Storage Correspondence
- File Backup
-
Protection
- CPU Protection
- Memory Protection
- I/O Protection
- File Protection
- Resource Protection
-
Networking
Operating System Services
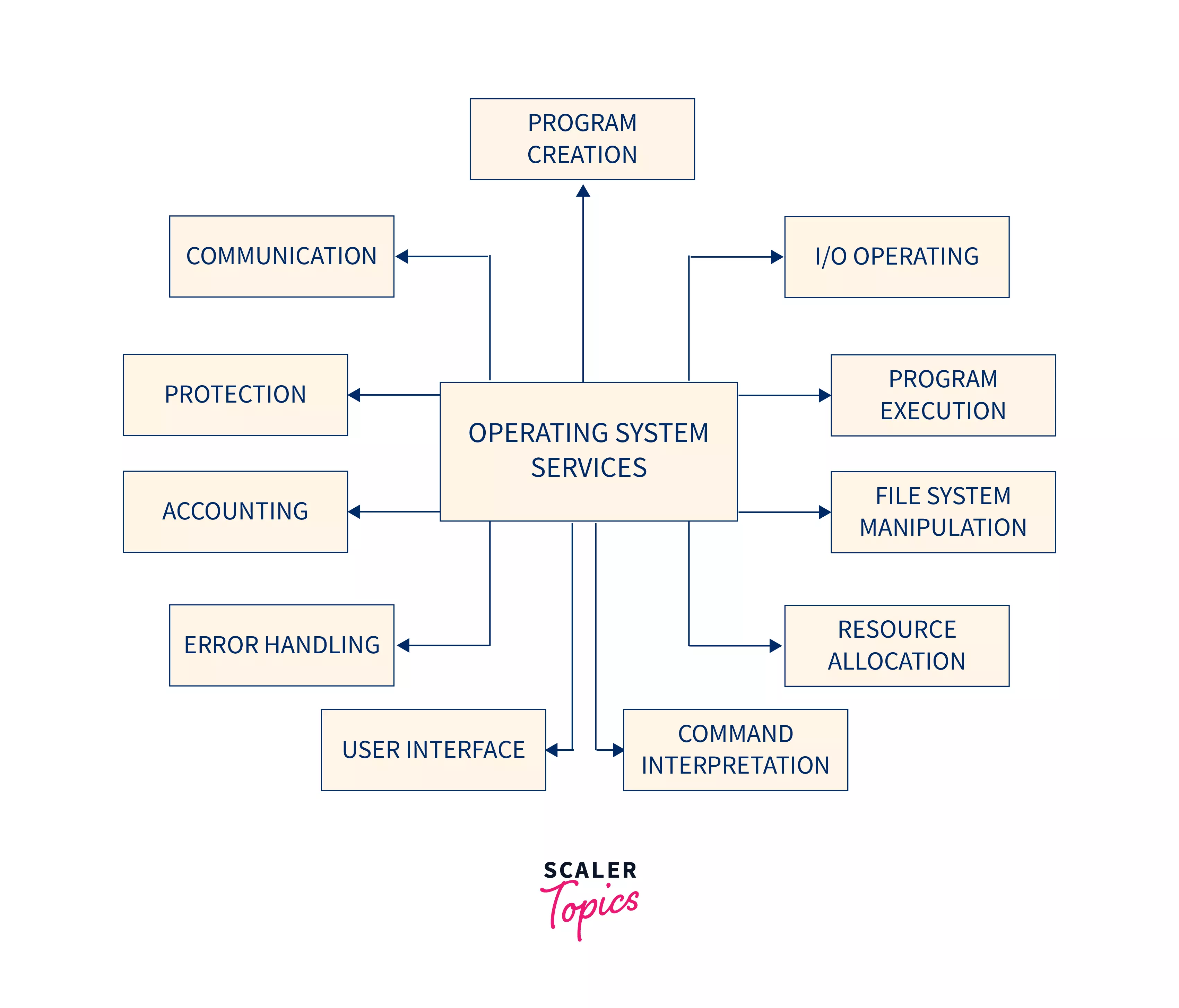
- Program Execution: Load, execute, and terminate programs.
- I/O Operations: Provide interfaces for I/O operations as users cannot directly interact with hardware.
- File System Manipulation: Create, read, write, and delete files.
- Inter-Process Communication (IPC): Enable communication between processes via shared memory or message passing.
- Error Handling:
- CPU or memory errors
- I/O errors
- User program errors
- Protection and consistency errors
- Resource Allocation: Efficiently allocate resources to processes using a scheduler, considering CPU speed, necessary jobs, usage registers, and managing devices like plotters and modems.
- Accounting: Track resource usage by users for billing or system improvement.
- Protection: Implement authentication, authorization, access control, and secure external I/O devices like modems and network interfaces.
System Calls
System calls serve as an interface between running programs (processes) and the operating system (OS). They typically use assembly language commands, though some systems allow high-level languages to call system calls directly. These calls usually resemble function calls and use special runtime routines to generate system calls or inline system calls.
Example Scenario: File Operations
Consider coding an editor that reads data from one file and copies it to another:
- Input and Output File Names: System calls for displaying messages on the screen and reading characters from the keyboard.
- Open Input File and Create Output File: System calls to handle file operations.
- Read System Call: Reads data from the input file.
- Write System Call: Writes data to the output file.
- Close System Call: Closes both input and output files.
- Exit System Call: Ends the program.
Users typically do not see these details as runtime support systems provide simple interfaces for most programming languages to call system calls.
Passing Parameters to System Calls
System parameters are usually passed to the OS through:
- Registers: Passing parameters directly in registers.
- Memory Block: Storing parameters in a memory block and storing the block's address in a register.
- Stack: Storing parameters on the stack.
System Call Types
- Process Control: End, abort, create, load, execute, and terminate processes; read/write process attributes; wait for time, events, or other processes; allocate and release memory.
- File Management: Create, delete, open, close, read, write, relocate, and get/set file attributes.
- Device Management: Request, release, read, write, manage device operations, and get/set device attributes; logically connect and disconnect devices.
- Information Maintenance: Get and set time or date; get and set system data; get and set process, file, or device attributes.
- Communications: Create, delete, send, and receive messages; establish and terminate connections.
Command Interpreter System Program
The command interpreter system, or shell (UNIX), serves as the interface between users and the operating system. It reads and executes commands entered by the user, typically upon login or job start.
There are two primary implementation methods:
-
Built-in Commands:
- Commands are embedded within the interpreter itself.
- For example, entering
delete file.txtexecutes the internaldeletefunction directly.
-
External Programs:
- Commands are interpreted as external programs.
- For example, entering
delete file.txtprompts the interpreter to search, load and execute a separate program file nameddelete, passingfile.txtas an argument.
An example scenario illustrates the difference:
Deleting file.txt:
-
Built-in:
- Type
delete file.txt. - The shell executes the built-in delete function immediately.
- Type
-
External:
- Type
delete file.txt. - The shell loads and runs the
deleteprogram (a file), which handles the file deletion.
- Type
The game Lethal Company features a command-line interface for interacting with the game world, which is pretty fun.

System Structure
MS-DOS (Micro Soft-Diskette Operating System)
MS-DOS operates without dual-mode functionality or hardware protection, which limits its control over hardware and security capabilities.

UNIX
UNIX has a modular structure with a core kernel and system programs. The kernel manages interfaces and device drivers, while system programs handle file systems, CPU scheduling, memory management, and other services.
- Kernel: Manages system resources and hardware.
- Shell: The user interface for command execution.
Layered Approach
The layered approach to operating system design structures the OS into multiple layers, each built on top of the lower layers. Each layer provides specific functionality and interacts only with the layer directly below it, allowing for modularity and easier debugging. The bottom layer (layer 0) is the hardware, and the highest layer (layer N) is the user interface.
However, this approach has some challenges:
- Complex Design: Structuring an OS in layers requires careful planning to ensure efficient communication and functionality.
- Performance Overhead: Multiple layers can introduce performance overhead due to added levels of abstraction.
- Dependency Management: Ensuring proper dependencies and interactions between layers can be complex.
Virtual Machines
With CPU scheduling and virtual memory, an operating system can create multiple virtual machines (VMs) on a single physical machine. Each VM operates with its own OS instance, applications, and resources, giving the illusion of multiple independent machines on the same hardware.
The benefits of virtual machines include:
- Isolation: Each VM operates independently, preventing issues in one VM from affecting others.
- Security: Enhanced security as each VM is isolated from others.
- Resource Allocation: Efficient use of hardware by allocating resources as needed.
- Flexibility: Different OS environments can run on the same hardware.
The challenges of virtual machines include:
- Accuracy: Creating an accurate low-level machine copy is complex.
- User Mode Limitation: VMs run in user mode, necessitating further separation of virtual kernel and user modes.
- Communication: Facilitating communication between VMs can be difficult.
Virtual machines utilize spooling and file systems to manage multiple I/O devices efficiently, creating virtual readers and writers. This isolation ensures that errors or modifications within a VM do not crash the entire physical system.
Java Virtual Machine (JVM)
The Java Virtual Machine (JVM) executes Java bytecode, which is generated by compiling Java source files. The JVM includes several key components:
- Class Loader: Loads class files into the JVM.
- Class Verifier: Ensures that loaded classes are valid and do not violate Java's security constraints, preventing issues like buffer overflow or underflow.
- Garbage Collection: Automatically manages memory by removing objects that are no longer in use.
Java Interpreter and Just-In-Time (JIT) Compiler
-
Java Interpreter: A software module that converts Java bytecode into machine code at runtime. It reads and executes one bytecode instruction at a time, which can be slower.
-
Just-In-Time (JIT) Compiler: Converts Java bytecode into machine code at runtime, but unlike the interpreter, it compiles entire blocks of bytecode to machine code before execution. This makes the execution faster because the compiled code can be directly executed by the CPU without further interpretation.
The JIT compiler improves performance significantly compared to the interpreter by optimizing the bytecode into highly efficient machine code.
Mechanism and Policy
Operating systems separate mechanism and policy to provide flexibility and ease of modification. Mechanisms define how tasks are performed, while policies define what tasks should be done. This separation allows policies to change without altering the underlying mechanisms, enhancing system adaptability and maintainability.
Microkernel
The microkernel architecture reduces the kernel's size and complexity by moving non-essential components to user space. The microkernel includes only essential functions such as:
- Address Spaces: Memory management.
- Inter-Process Communication (IPC).
- Basic Scheduling.
Other services, like device drivers and file systems, run as user-level processes. Communication between these components occurs through message passing, which can be slower than direct function calls.
Advantages:
- Scalability & Flexibility: Easier to add new services without modifying the kernel. Simplifies updates and maintenance, allowing changes to services without impacting the core kernel.
- Reliability & Security: Isolating non-essential components improves system reliability and security. If a user-level service crashes, it does not affect the entire core kernel, and thus the system remains operational.
Disadvantages:
- Performance Overhead: Frequent context switches and message passing between user space and kernel space can lead to performance overhead compared to monolithic kernels.
- Complexity: Designing and implementing a microkernel is more complex due to the need to define and manage the communication between various services running in user space.
Conclusion
If you find it hard to absorb the information, try to review the overall concepts by watching the video below. 🧠
In this section, we explored the Operating System Structure, focusing on its key components such as process management, memory management, and I/O management, which ensure efficient and secure system operations.
We discussed Operating System Services, including program execution, I/O operations, file system management, inter-process communication, error handling, resource allocation, accounting, and protection.
The role of System Calls was examined, highlighting their importance as an interface between running programs and the OS, enabling essential operations like process control, file management, and device management.
The Command Interpreter System Program (or shell) was discussed, emphasizing its function as the user interface for command execution, either through built-in commands or external programs.
We reviewed the System Structure of MS-DOS and UNIX, illustrating their approaches to managing hardware and software resources.
The Layered Approach in OS design was covered, showing how it organizes the system into modular layers, each providing specific functions.
We explored Virtual Machines, which create isolated environments on a single physical machine, offering benefits like isolation and flexibility, while presenting challenges like accurate low-level replication.
The Java Virtual Machine (JVM) was discussed, detailing its role in running Java bytecode, ensuring platform independence, and using interpreters and Just-In-Time (JIT) compilers for efficient execution.
The Microkernel Architecture was examined, highlighting its benefits in scalability, reliability, and flexibility by isolating non-essential components and reducing kernel size.
Finally, we covered the separation of Mechanism and Policy in OS design, which allows for flexible policy changes without altering the underlying mechanisms, enhancing system adaptability.
Nice work! You've gained a comprehensive understanding of Operating System Structure and its key components. Keep exploring to deepen your knowledge and apply these concepts in practice. 🚀